We’re talking about security in the cloud
Over Exposure
Let’s put it this way, what do you worry about exposing? What are your most valuable assets? Your Social Security Number? Your bank account information? Private documents, or photographs? Your crypto seed phrase? If you manage a company, or are responsible for the safekeeping of data, you may worry about the same types of information being compromised, but on a broader scale. You’ve been entrusted by your customers with the protection of their data.
As consumers, we take the security of our data for granted. More and more often these days that data is stored in the cloud. A number of vendors offer services which allow customers to backup data from their local computers to the cloud. Think of it as a virtual hard drive in the sky. This is advertised as a safe and convenient way to protect your data. Convenient, yes. You can recover a file that you’ve accidentally deleted. You can restore an entire hard drive whose data was corrupted.
But is it safe? You are provided with a lock and key. The key is, typically, a username and password. It is encrypted and known only to you. That’s why security experts recommend keeping your password secure. If someone gains access to your password, they have the virtual key to your virtual house.
You know all this. Your password to the backup cloud service is 16 characters long, contains uppercase and lowercase letters, numbers and a couple special characters. You change it every six months because you know that makes it harder for the hacker. It is different from your other passwords – you don’t use the same password for multiple sites. What could go wrong?
Some companies offer what they’ve branded as a “Personal Cloud.” Western Digital is one of those companies that provide an easy way to backup your data to your personal space in a cloud. It’s networked storage available over the internet. It plugs into your Wi-Fi router so you can access it from anywhere inside your network. Conveniently, because it’s also connected to the internet, you can access your personal data from anywhere on the internet. With convenience comes risk.
A Compromising Position
Earlier this year, hackers broke into Western Digital’s systems and were able to download approximately 10 Tb of data. The black mailers then held the data for ransom and tried to negotiate a deal north of US $10,000,000 for the safe return of the data. Data is like oil. Or maybe gold is a better analogy. One of the hackers spoke on the condition of anonymity. Ha! TechCrunch interviewed him while he was in the process of this business deal. What is interesting is that the data that was compromised included Western Digital’s code-signing certificate. This is the technological equivalent of a retina scan. The certificate is intended to positively identify the owner or bearer. With this virtual retina scan, no password is required for access to “secured” data. In other words, with this certificate this black hat businessman can walk right in the front door of the digital palace.
Western Digital declined to comment in response to the hacker’s claims that they were still in WD’s network. The unnamed hacker expressed disappointment that representatives at Western Digital would not return his calls. Officially, in a press release, Western Digital announced that, “Based on the investigation to date, the Company believes the unauthorized party obtained certain data from its systems and is working to understand the nature and scope of that data.” So, Western Digital is mum, but the hacker is blabbing. As for how they did it, the hacker describes how they exploited known vulnerabilities and were able to gain access to data in the cloud as a global administrator.
A global administrator, by nature of the role, has access to everything. He doesn’t need your password. He has the master key.
Western Digital is Not Alone
A survey last year found that 83% of the companies surveyed had had more than one data breach, 45% of which were cloud-based. The average cost of a data breach in the United States was US $9.44 million. Costs were broken down into four cost categories — lost business, detection and escalation, notification and post breach response. (I’m not sure what category the data ransom is in. It isn’t clear if any of the respondents did pay ransom demands.) The average time it takes an organization to identify and respond to a data breach is about 9 months. It isn’t a surprise, then, that several months after Western Digital first acknowledged a data breach, they are still investigating.
It’s hard to say exactly how many companies have had data breaches. I know one large privately held company that was attacked by ransomware. The owners refused to negotiate and did not pay. That meant, instead, lost emails and data files. They chose to rebuild everything from uninfected backups and reinstall software. There was significant down-time and lost productivity. This event was never in the media. That company was lucky because 66% of small to medium sized companies who are attacked by ransomware end up going out of business within 6 months.
- 30,000 websites are hacked daily
- 4 million files are stolen every day
- 22 billion records were breached in 2021
If you’ve ever done business with, or used the services of Capital One, Marriott, Equifax, Target or Uber, it’s possible that your password was compromised. Each of these major companies suffered a significant data breach.
- Capital One: A hacker gained access to 100 million customers and applicants by exploiting a vulnerability in the company’s cloud infrastructure.
- Marriott: A data breach exposed information on 500 million customers (this breach went undetected for 4 years).
- Equifax: Personal info in the cloud on 147 million customers was exposed.
- Target: Cybercriminals accessed 40 million credit card numbers.
- Uber: Hackers compromised a developer’s laptop and gained access to 57 million users and 600,000 drivers.
- LastPass[1]: Hackers stole 33 million customers’ vault data in a cloud storage breach for this password manager company. The attacker gained access to Lastpass’ cloud storage using a “cloud storage access key and dual storage container decryption keys” stolen from its developer environment.
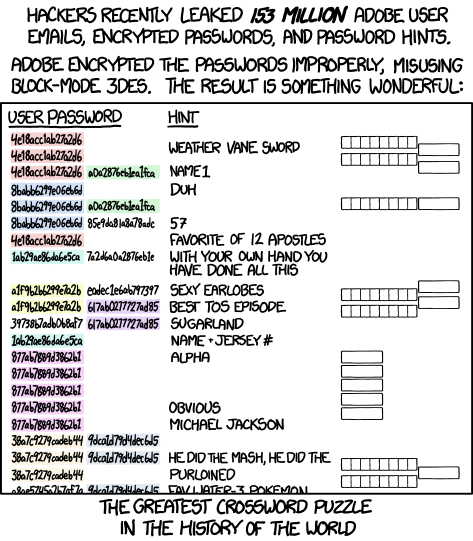
You can check to see if you’ve been exposed in a data breach at this website: have i been pwned? Type in your email address and it will show you how many data breaches the email address has been found in. For example, I typed in one of my personal email addresses and found that it had been a part of 25 different data breaches, including Evite, Dropbox, Adobe, LinkedIn and Twitter.
Thwarting Unwanted Suitors
There may never be a public acknowledgement by Western Digital of exactly what happened. The incident does illustrate two things: data in the cloud is only as secure as its keepers and the keepers of the keys need to be especially careful. To paraphrase the Peter Parker Principle, with root access comes great responsibility.
To be more precise, a root user and a global administrator are not exactly the same. Both have much power but should be separate accounts. The root user owns and has access to the corporate cloud account at the lowest level. As such, this account could delete all data, VMs, customer information — everything that a business has secured in the cloud. In AWS, there are only 10 tasks, including setting up and closing your AWS account, that truly require root access.
Administrator accounts should be created to perform administrative tasks (duh). There are usually multiple Administrator accounts which are usually person-based, unlike the single root account. Because Administrator accounts are tied to an individual, you can easily monitor who made what changes in the environment.
Least Privilege for Maximum Security
The data breach survey studied the impact of 28 factors on the severity of a data breach. The use of AI security, a DevSecOps approach, employee training, identity and access management, MFA, security analytics all had a positive impact in reducing the average dollar amount lost in an incident. Whereas, compliance failures, security system complexity, security skills shortage, and cloud migration were factors which contributed to higher net increase in the average cost of a data breach. 
As you migrate to the cloud, you need to be more vigilant than ever in protecting your data. Here are some additional ways to reduce your risk and run a safer environment from a security standpoint:
1. Muli-factor Authentication: enforce MFA for root and all Administrator accounts. Even better, use a physical hardware MFA device. A potential hacker would need not only the account name and password, but also the physical MFA which generates a synchronized code.
2. Power in small numbers: Limit who has access to the root. Some security experts suggest no more than 3 users. Manage root user access assiduously. If you execute identity management and off-boarding nowhere else, do it here. If one in the circle of trust leaves the organization, change the root password. Recover the MFA device.
3. Default Account Privileges: When provisioning new user accounts or roles, ensure that they are granted minimal privileges by default. Start with a minimal access policy and then grant additional permissions as needed. The principle of providing the least security to accomplish a task is a model that will pass SOC2 security compliance standards. The concept is that any user or application should have the minimum security required to perform the required function. The higher the privilege that is compromised, the greater the risk. Conversely, the lower the privilege exposed, the lower the risk.
4. Auditing Privileges: Regularly audit and review the privileges assigned to users, roles, and accounts within your cloud environment. This ensures that individuals have only the necessary permission to perform their designated tasks.
5. Identity Management and Just-in-time Privileges: Identify and revoke any excessive or unused privileges to minimize the risk of unauthorized access. Only provide access rights to users when they require them for a specific task or a limited period. This minimizes the attack surface and reduces the window of opportunity for potential security threats. 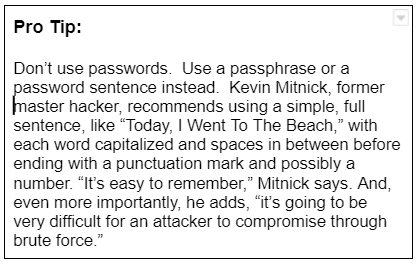
6. Embedded credentials: Prohibit the hard-coding of unencrypted authentication (username, password, access keys) in scripts, jobs, or other code. Instead look into a secrets manager that you can use to programmatically retrieve credentials.
7. Infrastructure-as-Code (IaC) Configuration: Adhere to security best practices when configuring your cloud infrastructure using IaC tools like AWS CloudFormation or Terraform. Avoid granting public access by default and restrict access to resources to only trusted networks, users, or IP addresses. Utilize fine-grained permissions and access control mechanisms to enforce the principle of least privilege.
8. Logging of Actions: Enable comprehensive logging and monitoring of actions and events within your cloud environment. Capture and analyze logs for any unusual or potentially malicious activities. Implement robust log management and security information and event management (SIEM) solutions to detect and respond to security incidents promptly.
9. Regular Vulnerability Assessments: Perform regular vulnerability assessments and penetration testing to identify security weaknesses in your cloud environment. Patch and remediate any identified vulnerabilities promptly. Keep track of security updates and patches released by your cloud provider and ensure they are applied promptly to protect against known threats.
10. Education and Training: Promote a culture of security awareness and provide regular training to employees regarding the importance of the principle of least privilege. Educate them about the potential risks associated with excessive privileges and the best practices to follow when accessing and managing resources within the cloud environment.
11. Patches and Updates: Reduce vulnerabilities by regularly updating all server software. Keep your cloud infrastructure and associated applications up to date to protect against known vulnerabilities. Cloud providers often release security patches and updates, so staying current with their recommendations is crucial.
Trust
It comes down to trust – providing only those in your organization the trust to accomplish the tasks they need to do to get their job done. Security experts recommend Zero Trust. The Zero Trust security model is based on three key principles:
- Verify explicitly – use all available data points to validate a user’s identity and access.
- Use least-privilege access – just in time and just enough security.
- Assume breach – encrypt everything, employ proactive analytics and have emergency response in place.
As a consumer of the cloud and cloud services, it also comes down to trust. You have to ask yourself, “do I trust my vendor to store my precious data in the cloud?” Trust, in this case, means that you rely on that company, or one like it, to manage security as we’ve described above. Alternatively, if you answer in the negative, are you prepared to perform the same types of security management activity in your home environment. Do you trust yourself?
As a company providing services in the cloud, customers have placed their trust in you to safeguard their data in your cloud infrastructure. It’s an ongoing process. Stay informed about emerging threats, adapt your security measures accordingly, and collaborate with experienced professionals or security consultants to ensure the utmost protection for your business in the ever-evolving cloud landscape.
- https://www.bleepingcomputer.com/news/security/lastpass-hackers-stole-customer-vault-data-in-cloud-storage-breach/ ↑


